- What is an example of an M2M connection in the IoT?A user sends an email over the Internet to a friend.
Sensors in a warehouse communicate with each other and send data to a server block in the cloud.*
Redundant servers communicate with each other to determine which server should be active or standby.
An automated alarm system in a campus sends fire alarm messages to all students and staff.
The Internet of Things (IoT) connects devices that traditionally are not connected to the Internet, such as sensors and actuators. A machine-to-machine (M2M) connection is unique to the IoT in that devices are connected together and communicate with each other. These devices can send data to a server block in the cloud for analysis and further operation change.
- What is the term for the extension of the existing Internet structure to billions of connected devices?M2M
digitization
IoT*
SCADA
The Internet of Things (IoT) refers to the interconnection of billions of things, or “smart dust.” SCADA refers to a type of IoT system applied to the industrial Internet. Digitization has several meanings. It can refer to the process of converting analog to digital, or it can refer to the process by which an organization modernizes by planning and ultimately building, a sophisticated and forward-thinking IT network ecosystem that will allow for greater connectivity, productivity, and security. Finally, M2M refers to communication from machine to machine.
- Which statement describes the Cisco IoT System?It is a switch operating system to integrate many Layer 2 security features.
It is an advanced routing protocol for cloud computing.
It is an infrastructure to manage large scale systems of very different endpoints and platforms.*
It is a router operating system combining IOS and Linux for fog computing.
Cisco developed the Cisco IoT System to help organizations and industries adopt IoT solutions. The IoT system provides an infrastructure to manage large scale systems of very different endpoints and platforms, and the huge amount of data that they create. Cisco IOx combines IOS and Linux to support fog computing.
- Which three network models are described in the fog computing pillar of the Cisco IoT System? (Choose three.)fog computing*
client/server*
P2P
cloud computing*
peer-to-peer
enterprise WAN
The network models describe how data flows within a network. The network models described in the Fog computing pillar of the Cisco IoT System include:
Client/Server model – Client devices request services of servers. Servers are often located locally and managed by the organization.
Cloud computing model – a newer model where servers and services are dispersed globally in distributed data centers. Data is synchronized across multiple servers.
Fog computing – This model identifies a distributed computing infrastructure closer to the network edge. It enables edge devices to run applications locally and make immediate decisions.
- Which IoT pillar extends cloud connectivity closer to the network edge?network connectivity pillar
fog computing pillar*
management and automation pillar
application enablement platform pillar
By running distributed computing infrastructure closer to the network edge, fog computing enables edge devices to run applications locally and make immediate decisions.
- Which cybersecurity solution is described in the security pillar of the Cisco IoT System to address the security of power plants and factory process lines?IoT network security
cloud computing security
operational technology specific security*
IoT physical security
The Cisco IoT security pillar offers scalable cybersecurity solutions that include the following:
Operational Technology specific security – the hardware and software that keeps the power plants running and manages factory process lines
IoT Network security – network and perimeter security devices such as switches, routers, and ASA Firewall devices
IoT Physical Security – include Cisco Video Surveillance IP Cameras that enable surveillance in a wide variety of environments
- Which cloud computing opportunity would provide the use of network hardware such as routers and switches for a particular company?infrastructure as a service (IaaS)*
software as a service (SaaS)
browser as a service (BaaS)
wireless as a service (WaaS)
This item is based on information contained in the presentation.
Routers, switches, and firewalls are infrastructure devices that can be provided in the cloud.
- What technology allows users to access data anywhere and at any time?Cloud computing*
virtualization
micromarketing
data analytics
Cloud computing allows organizations to eliminate the need for on-site IT equipment, maintenance, and management. Cloud computing allows organizations to expand their services or capabilities while avoiding the increased costs of energy and space.
- The exhibit is not required to answer the question. The exhibit shows a fog covering trees on the side of a mountain.What statement describes Fog computing? It requires Cloud computing services to support non-IP enabled sensors and controllers.
It supports larger networks than Cloud computing does.
It creates a distributed computing infrastructure that provides services close to the network edge.*
It utilizes a centralized computing infrastructure that stores and manipulates big data in one very secure data center.
Three of the defining characteristics of Fog computing are as follows:
its proximity to end-users
its distributed computing infrastructure that keeps it closer to the network edge
its enhanced security since data is not released into the Cloud
- Which Cloud computing service would be best for a new organization that cannot afford physical servers and networking equipment and must purchase network services on-demand?ITaaS
SaaS
PaaS
IaaS*
Infrastructure as a service (IaaS) provides an environment where users have an on-demand infrastructure that they can install any platform as needed.
- Which cloud model provides services for a specific organization or entity?a public cloud
a hybrid cloud
a private cloud*
a community cloud
Private clouds are used to provide services and applications to a specific organization and may be set up within the private network of the organization or managed by an outside organization.
- How does virtualization help with disaster recovery within a data center?improvement of business practices
supply of consistent air flow
support of live migration*
guarantee of power
Live migration allows moving of one virtual server to another virtual server that could be in a different location that is some distance from the original data center.
- What is a difference between the functions of Cloud computing and virtualization?Cloud computing separates the application from the hardware whereas virtualization separates the OS from the underlying hardware.*
Cloud computing requires hypervisor technology whereas virtualization is a fault tolerance technology.
Cloud computing utilizes data center technology whereas virtualization is not used in data centers.
Cloud computing provides services on web-based access whereas virtualization provides services on data access through virtualized Internet connections.
Cloud computing separates the application from the hardware. Virtualization separates the OS from the underlying hardware. Virtualization is a typical component within cloud computing. Virtualization is also widely used in data centers. Although the implementation of virtualization facilitates an easy server fault tolerance setup, it is not a fault tolerance technology by design. The Internet connection from a data center or service provider needs redundant physical WAN connections to ISPs.
- Which two business and technical challenges does implementing virtualization within a data center help businesses to overcome? (Choose two.)physical footprint*
server hardware needs
virus and spyware attacks
power and air conditioning*
operating system license requirements
Traditionally, one server was built within one machine with one operating system. This server required power, a cool environment, and a method of backup. Virtualized servers require more robust hardware than a standard machine because a computer or server that is in a virtual machine commonly shares hardware with one or more servers and operating systems. By placing multiple servers within the same physical case, space is saved. Virtualized systems still need the proper licenses for operating systems or applications or both and still need the proper security applications and settings applied.
- Which statement describes the concept of cloud computing?separation of operating system from hardware
separation of management plane from control plane
separation of application from hardware*
separation of control plane from data plane
Cloud computing is used to separate the application or service from hardware. Virtualization separates the operating system from the hardware.
- Which is a characteristic of a Type 2 hypervisor?best suited for enterprise environments
installs directly on hardware
does not require management console software*
has direct access to server hardware resources
Type 2 hypervisors are hosted on an underlaying operating system and are best suited for consumer applications and those experimenting with virtualization. Unlike Type 1 hypervisors, Type 2 hypervisors do not require a management console and do not have direct access to hardware.
- Which is a characteristic of a Type 1 hypervisor?does not require management console software
installed directly on a server*
installed on an existing operating system
best suited for consumers and not for an enterprise environment
Type 1 hypervisors are installed directly on a server and are known as “bare metal” solutions giving direct access to hardware resources. They also require a management console and are best suited for enterprise environments.
- How is the control plane modified to operate with network virtualization?Control plane redundancy is added to each network device.
The control plane on each device is interconnected to a dedicated high-speed network.
A hypervisor is installed in each device to allow multiple instances of the control plane.
The control plane function is consolidated into a centralized controller.*
In network virtualization design, the control plane function is removed from each network device and is performed by a centralized controller. The centralized controller communicates control plane functions to each network device and each device focuses on forwarding data.
- Which technology virtualizes the network control plane and moves it to a centralized controller?IaaS
SDN*
fog computing
cloud computing
Networking devices operate in two planes: the data plane and the control plane. The control plane maintains Layer 2 and Layer 3 forwarding mechanisms using the CPU. The data plane forwards traffic flows. SDN virtualizes the control plane and moves it to a centralized network controller.
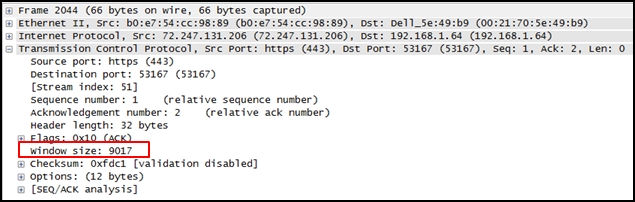
- Which two layers of the OSI model are associated with SDN network control plane functions that make forwarding decisions? (Choose two.)Layer 1
Layer 2*
Layer 3*
Layer 4
Layer 5
The SDN control plane uses the Layer 2 ARP table and the Layer 3 routing table to make decisions about forwarding traffic.
- What pre-populates the FIB on Cisco devices that use CEF to process packets?the adjacency table
the routing table*
the DSP
the ARP table
CEF uses the FIB and adjacency table to make fast forwarding decisions without control plane processing. The adjacency table is pre-populated by the ARP table and the FIB is pre-populated by the routing table.
- Which type of hypervisor would most likely be used in a data center?Type 1*
Hadoop
Nexus
Type 2
The two type of hypervisors are Type 1 and Type 2. Type 1 hypervisors are usually used on enterprise servers. Enterprise servers rather than virtualized PCs are more likely to be in a data center.
- What component is considered the brains of the ACI architecture and translates application policies?the Application Network Profile endpoints
the Nexus 9000 switch
the hypervisor
the Application Policy Infrastructure Controller*
The ACI architecture consists of three core components: the Application Network Profile, the Application Policy Infrastructure Controller, which serves as the brains of the ACI architecture, and the Cisco Nexus 9000 switch.
- Fill in the blank.
In an IoT implementation, devices will be connected to a
network to share the same infrastructure and to facilitate communications, analytics, and management.
Correct Answer: converged
Currently, many things are connected using a loose collection of independent use-specific networks. In an IoT implementation, devices will be connected to a converged network to share the same infrastructure and to facilitate communications, analytics, and management.
- Fill in the blank.
In a scenario where a user with a laptop running the Mac OS installs a Windows virtual OS instance, the user is implementing a Type
hypervisor.
Correct Answer: 2
Type 2 hypervisors, also know as hosted hypervisors, are installed on top of an existing operating system, such as Mac OS, Windows, or Linux.